Exploring Serilog v2 - Using Splunk with the File Sink and Docker
I have had a few questions recently about how to setup Docker with Serilog and Splunk when logging to a file. Generally I opt to use the HTTP Event Collector however there are some situations that warrant logging to a file.
A simple way to get logging out via a file to Splunk in Docker is via a shared volume. As I mentioned I can think of better production approaches however here is some quick setups to get up and running.
First create a few files and setup the project.
mkdir docker-example
cd docker-example
touch docker-compose.yml
touch Dockerfile
# Setup the app
mkdir example
cd example
dotnet new console
dotnet add package Serilog
dotnet add package Serilog.Sinks.Console
dotnet add package Serilog.Sinks.FileOpen Program.cs in your favourite editor and update accordingly. In this case we are going to log to a text file called mylog.txt.
using System;
using Serilog;
using System.Collections.Generic;
using System.Linq;
using System.IO;
namespace example
{
class Program
{
static void Main(string[] args)
{
Log.Logger = new LoggerConfiguration()
.WriteTo.Console()
.WriteTo.File(path:"mylog.txt", buffered: true)
.CreateLogger();
foreach (var i in Enumerable.Range(0, 1000))
{
Log.Information("Hello world {Counter}", i * x);
}
Log.CloseAndFlush();
}
}
} Next add the build steps to the multi-stage Dockerfile. Note we are pubishing the build output to the sample folder.
FROM microsoft/dotnet:2.1-sdk AS build
WORKDIR /sample
ADD . /sample
RUN dotnet restore
RUN dotnet publish -c Release -o out
FROM microsoft/dotnet:2.1-runtime AS runtime
WORKDIR /sample
COPY --from=build /sample/out ./
ENTRYPOINT ["dotnet", "example.dll"]Now we need to setup the app, with a Splunk instance to ingest the logs. Update the docker-compose.yml as below. This setup includes a shared volume applogs that will be mounted on both containers.
version: '3'
services:
myexample:
image: myexample
volumes:
- applogs:/sample
splunkenterprise:
image: splunk/splunk:7.1.0
environment:
SPLUNK_START_ARGS: --accept-license --answer-yes --seed-passwd changeme
SPLUNK_ENABLE_LISTEN: 9997
SPLUNK_ADD: tcp 1514
SPLUNK_ADD_1: monitor /sample/*
ports:
- "8001:8000"
- "9997:9997"
- "8088:8088"
- "8089:8089"
- "1514:1514"
volumes:
- applogs:/sample/logs
volumes:
applogs:Run it up with docker-compose up and then open a browser at http://locahost:8001.
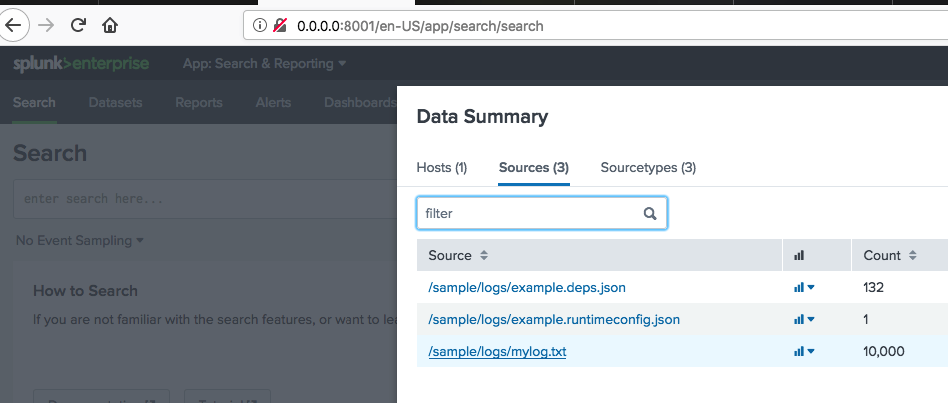
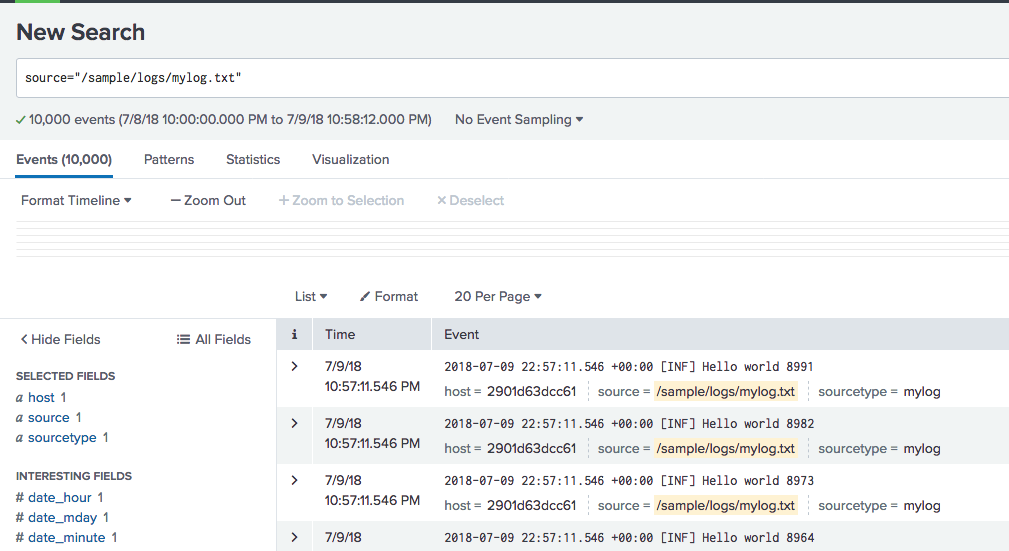
Sources should now show the file source, and events should be available.
Sources
Events
This is a simple way of getting log files using Serilog, into Splunk when using Docker.
